From the Defcon voting village, to the voting machine show in Harrisburg, to every voting machine I have ever seen or worked with for over 40 years; all of them has an FCC Part 15 notice on them which states:
This device complies with Part 15 of the FCC Rules. Operation is subject to the following
two conditions:
1) This device may not cause harmful interference.
2) This device must accept any interference received, including interference
that may cause undesired operation.
And therein, in part 2 is the problem. Since all electronic voting machines are considered “critical infrastructure”, we want then to work as intended ALL the time. Yet, part 2 suggests they must accept interference which causes an undesirable operation.
So, one day I decided to put this denial of service theory to a test. Subject machine is a sacrificial Dell Latitude D620 running Windows XP sp3 using the benchtest suite included with HWINFO32. Here is what it looked like before I injected a 133 mhz signal into the laptop.
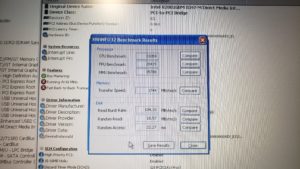
Here is what happened when I energized the signal generator.
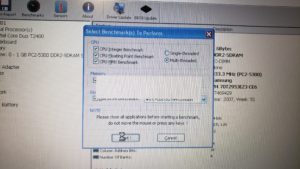
Note the blank space in the middle? The hour glass mouse pointer? It did this until I turned off the signal generator.
Now to be fair, this signal injection was deliberately done. But this could happen just as easily from random RF interference, because again voting machines are unshielded electronic devices and they must accept all interference whether intentional or not.
So if you see something, say something. It’s not likely to be a deliberate interference, but only an expert can tell the difference between accidental and deliberate interference. Vote as if your life and the lives of your family depend on it, because it does.
—